MAKE DATA YOUR

MAKE DATA YOUR

MAKE DATA YOUR

Advanced Data Management Platform for Today & Tomorrow
Imagine creating solutions that transform how we live, learn, work, and interact. How would your business grow? How could you change the world? LifeGraph® from BurstIQ raises your business IQ and your trust quotient to redefine what you thought was possible.
Advanced Data Management
Platform for Today & Tomorrow
Imagine creating solutions that transform how we live, learn, work, and interact. How would your business grow? How could you change the world? LifeGraph® from BurstIQ raises your business IQ and your trust quotient to redefine what you thought was possible.
Advanced Data Management
Platform for Today & Tomorrow
Imagine creating solutions that transform how we live, learn, work, and interact. How would your business grow? How could you change the world? LifeGraph® from BurstIQ raises your business IQ and your trust quotient to redefine what you thought was possible.
LifeGraph is a first-of-its-kind data management
platform that quickly:
1.
ELIMINATES DATA COMPLEXITY SO YOU CAN FOCUS ON
WHAT MATTERS
Finally solve age-old data problems and free teams to focus on higher-value work
2.
Organizes data how humans think
Uncover insights that traditional data management platforms can’t find
3.
Organizes Data How Machines Think
Ignite innovation with the power of collaborative intelligence
LifeGraph is a first-of-its-kind data
management platform that quickly:
1.
ELIMINATES DATA COMPLEXITY SO YOU CAN FOCUS ON WHAT MATTERS
Finally solve age-old data problems and free teams to focus on higher-value work
2.
Organizes data how humans think
Uncover insights that traditional data management platforms can’t find
3.
Organizes Data How Machines Think
Ignite innovation with the power of collaborative intelligence

LifeGraph is a first-of-its-kind data management platform that quickly:
1.
ELIMINATES DATA COMPLEXITY SO YOU CAN FOCUS ON WHAT MATTERS
Finally solve age-old data problems and free teams to focus on higher-value work
2.
Organizes data how humans think
Uncover insights that traditional data management platforms can’t find
3.
Organizes Data How Machines Think
Ignite innovation with the power of collaborative intelligence
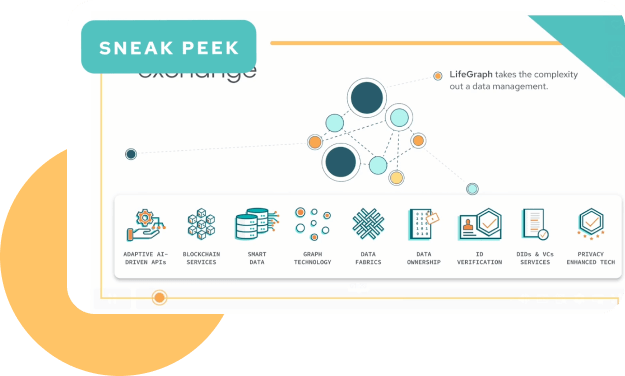
Conquer DATA CHAOS
It would take years and a multitude of vendors to stitch together what LifeGraph does for you in a single, powerful data management platform. Built from the ground up to ensure privacy and security, LifeGraph takes the frustration, time, and expense out of data management.
Conquer DATA CHAOS
It would take years and a multitude of vendors to stitch together what LifeGraph does for you in a single, powerful data management platform. Built from the ground up to ensure privacy and security, LifeGraph takes the frustration, time, and expense out of data management.
Conquer DATA CHAOS
It would take years and a multitude of vendors to stitch together what LifeGraph does for you in a single, powerful data management platform. Built from the ground up to ensure privacy and security, LifeGraph takes the frustration, time, and expense out of data management.
____Disparate Data
____Each Data Asset
____& Control to Build Trust
____Internal & External Systems
____Multi-Party Ecosystems
____Across Your Enterprise
____AI Applications
____Business Evolves

UNCOVER HIDDEN TRUTHS
Make Data More Useful for Humans and Machines
LifeGraph goes beyond the limitations of traditional databases with an interconnected and semantic approach to data. LifeGraph’s knowledge graph technology unveils meaningful connections across your data ecosystem. It also helps AI models better understand and interpret data for more accurate and trustworthy AI outputs. Move beyond analytics and embrace business-changing, knowledge-driven decisions.
SET THE PACE FOR TRANSFORMATION
Leverage Human + Machine Intelligence for Faster Innovation
Humans and AI can work together to extract valuable insights. While AI excels at analyzing large datasets, humans are better at understanding the context and meaning of the insights. By combining the two, we can achieve a powerful human-machine collaboration that marries deep human experience with the scope and scale of analysis delivered by AI.
We call this Collaborative Intelligence and it can turn your organization into an unstoppable force in the market. LifeGraph can help you tap into this power so you can:
Our Partners:
These great partners all made their impossible solutions possible with LifeGraph® data management technology.
We know you’re curious, so why not b
UNCOVER HIDDEN TRUTHS
Make Data More Useful for Humans and Machines
LifeGraph goes beyond the limitations of traditional databases with an interconnected and semantic approach to data. LifeGraph’s knowledge graph technology unveils meaningful connections across your data ecosystem. It also helps AI models better understand and interpret data for more accurate and trustworthy AI outputs. Move beyond analytics and embrace business-changing, knowledge-driven decisions.
SET THE PACE FOR TRANSFORMATION
Leverage Human + Machine Intelligence for Faster Innovation
Humans and AI can work together to extract valuable insights. While AI excels at analyzing large datasets, humans are better at understanding the context and meaning of the insights. By combining the two, we can achieve a powerful human-machine collaboration that marries deep human experience with the scope and scale of analysis delivered by AI.
We call this Collaborative Intelligence and it can turn your organization into an unstoppable force in the market. LifeGraph can help you tap into this power so you can:
Our Partners:
These great partners all made their impossible solutions possible with LifeGraph® data management technology. We know you’re curious, so why not b
UNCOVER HIDDEN TRUTHS
Make Data More Useful for Humans & Machines
LifeGraph goes beyond the limitations of traditional databases with an interconnected and semantic approach to data. LifeGraph’s knowledge graph technology unveils meaningful connections across your data ecosystem. It also helps AI models better understand and interpret data for more accurate and trustworthy AI outputs. Move beyond analytics and embrace business-changing, knowledge-driven decisions.
SET THE PACE FOR TRANSFORMATION
Leverage Human + Machine Intelligence for Faster Innovation
Humans and AI can work together to extract valuable insights. While AI excels at analyzing large datasets, humans are better at understanding the context and meaning of the insights. By combining the two, we can achieve a powerful human-machine collaboration that marries deep human experience with the scope and scale of analysis delivered by AI.
We call this Collaborative Intelligence and it can turn your organization into an unstoppable force in the market. LifeGraph can help you tap into this power so you can:
Our Partners:
These great partners all made their impossible solutions possible with LifeGraph® data management technology. We know you’re curious, so why not b